
Cross Site Scripting (XSS)
Howdy Hackers! With Cross Site Scripting (XSS) as the first tutorial, let’s start this new series/category dedicated to the core Ethical Hacking concepts. And with XSS being one of the most prevailing and dangerous vulnerability out there, what better to start with? Note that I’ll try to keep this as simple as humanly possible for you guys to easily understand the working principles behind the actual thing, so don’t worry!
Disclaimer : Everything mentioned in this article is purely for
Educational Purposes. Performing the same practically without
consent is considered and could land you up in jail. The HackrSpace
is strictly against such malformed practices and won't be responsible
for anything Unethical you might do with the shared knowledge.
Cross Site Scripting (XSS), What??
According to Wiki, “Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications. XSS enables attackers to inject client-side scripts into web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy. Cross-site scripting carried out on websites accounted for roughly 84% of all security vulnerabilities documented by Symantec as of 2007.”
According to OWASP, “Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it.”
In Layman’s terms, XSS or Cross Site Scripting is a Security flaw in a Web Application which allows a malicious user to run their own Hacking Code/Input into the vulnerable website. This code will then execute on every person’s browser whoever visits the page or the link and thus they basically get “Hacked” without even knowing what hit em’!
Okay, Cross Site Scripting! But How does it happen?

The Web usually works on something called the Same Origin Policy. What it states is that all the content on a webpage should have the same source. If this policy is not properly implemented, a malicious user is able to inject the webpage with data from any other evil Source. In most cases to steal Session Cookies or some User Credentials.
Sometimes, HTML code generates dynamically, Eg. Considering a simple calculation site with 2 input fields for numbers. The calculation code is generated dynamically and the sum is reflected back to the Screen. In such case, if the results being displayed back(Output) is not sanitized or encoded, the attacker could inject his own code. The Webpage will then execute the hacker’s code as well since it treats it as a valid input.
Types of Cross Site Scripting
There are basically 3 types of Cross Site Scripting(XSS) :
1. Reflected(Non-Persistent) Cross Site Scripting
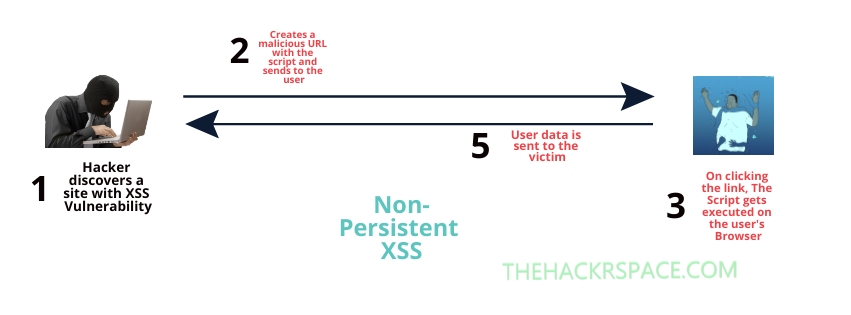
It is the simplest kind of XSS Vulnerability. It occurs when the injected script is not stored anywhere on the Website’s database but rather just reflects back off the Web Server in an immediate and unsafe way. Search results, form outputs, error messages or probably anything displaying back to the user after the Server processes it are all possible forms of the same.
Let’s take an example :
https://vulnerable-site.com/output?text=Security+is+a+myth
The Response is of the form :
<p> Security is a myth </p>
The application naively just throws back whatever the user enters back to the browser as the output without any kind of Sanitization.
So, a malicious user can easily construct something like :
https://vulnerable-site.com/output?text=<script>*evil+activity*</script>
The output will thus be :
<p><script>*evil+activity*</script></p>
Whenever the user clicks that crafted link(by some Social Engineering), the evil script is executed as it is loaded by the Browser to display it as the output and the hacker gets access to any data to which the end user has access to, without them even knowing anything.
2. Stored(Persistent) Cross Site Scripting
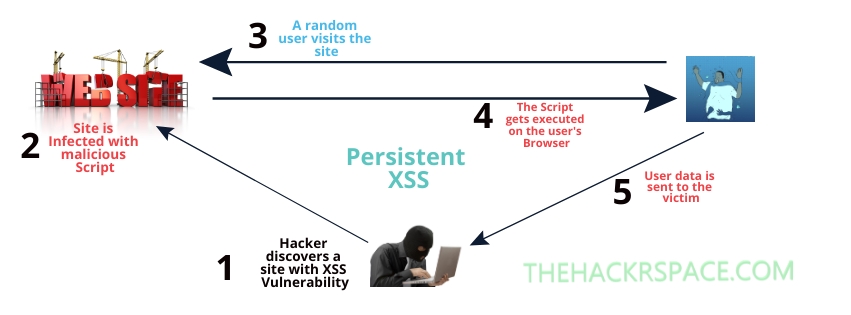
The whole concept remains the same, just this time, the malicious script/code is stored into the Website’s database. This greatly increases the potential impact of the attack as anyone who visit’s the Vulnerable site, ends up executing the script on their browser and gets Hacked!
An example in this case would be a vulnerable forum page which lets users post some kind of messages. Non sanitized stored inputs(data) allows a malicious user to inject some script(code) within the message. Later, whoever tries to view that message, the script is executed and the user’s Session cookies are stolen(or any of the other possible things) without even knowing what hit them.
3. DOM-Based Cross Site Scripting
It basically works the same way as Reflected XSS just differing on the working concept behind it.
DOM is the Document Object Model. It defines the logical structure of documents(Webpage) and the way of accessing and manipulating a Document. It basically represents the page so that programs can change the document structure, style, and content. The DOM represents the document as nodes and objects. Well it is a whole thing in itself and you could dive deep into it here with it’s W3c page.
Simply put, it is just a Programming Interface implemented by pretty much every Webpage which gives you the ability to access it.
Coming back to DOM based XSS, it occurs when the Client-Side Script of the Website writes HTML to the site’s DOM. Sounds confusing? let me just simply this for you. In this case, the data doesn’t go to the server for any processing, in fact the data never leaves the Browser at all. Everything just happens dynamically on the Browser itself.
For Example, imagine a site just displaying the data(text or numeric) along with you as you input the data into a form field. Unsafe encoding or processing of the data even on the client side, again leads to potential XSS dangers.
Umm…Sounds too technical, but what can you actually do with Cross Site Scripting?

The fun part eh? 😛 So, if you find a Website Vulnerable with Cross Site Scripting, you can :
- Impersonate a User (Session Hijacking)
- Get the User’s Credentials
- Performing actions on user’s behalf (CSRF attacks)
- Infect the Website with Malware and Trojans
- Deface the complete Website
- And more…
But the actual impact depends on the nature and functionality of the Website. General Public Info site? Banking site? Forum? You see where it’s going?
Awesome! But how do I check if the site is Vulnerable to Cross Site Scripting?

Here’s the interesting part, you can often check for Cross Site Scripting by trying to open a pop-up box on the particular webpage you’re trying to test.
But where to insert the script? Look for ways to input data into the Webpage. Search Box, Forms, Directly into the URL, Comments, Login, pretty much anything where a user can input data is a potential Attack Surface! And for what to inject, just try injecting the basic pop-up alert box as follows :
<script>alert("Hackable!")</script>
Keep in mind that most of the giant Websites won’t normally allow such basic XSS due to proper validations and Firewalls. But nonetheless it is still one of the most common Web App Vulnerabilities even today, so never know!
Also, you could refer to this XSS Cheat Sheet from OWASP for some advanced scripts to try bypassing the encoding and filters.
Conclusion…

So, I know it was a bit too technical and you guys wanted me to continue with the Kali and Android Series, but for the next part it would just have been a shut your brain and blindly follow kind of a thing. And that of course ain’t no fun. Thus for you guys to also understand the working concept behind the whole thing, is the reason for this New Category. Moreover, this is the actual Hacking part and you’ll eventually understand why stuff breaks! Oh and of course, do feel free to comment down below for any doubts or suggestions!
Because, Hacking you see, isn’t just a click-and-poof thing as in the movies, it’s way far beyond. But nonetheless it’s an awesome journey. We my friends, are the Digital Ninjas of this era trying to defy the already assumed unbreakable rules! :B More Awesome stuff coming soon! So stay Tuned and Happy Hacking 😀

It is really a great and helpful piece of information. I’m glad that you shared this helpful info with us. Please keep us up to date like this. Thanks for sharing.
Thanks You 😀 and will surely do!
What抯 Happening i am new to this, I stumbled upon this I have found It positively useful and it has helped me out loads. I hope to contribute & aid other users like its aided me. Good job.
Keep Sharing. Keep Helping 🙂
I have learn several excellent stuff here. Certainly value bookmarking for revisiting. I wonder how much effort you set to make this kind of wonderful informative site.
Thanks mate! Yeah, quite an effort as a One-Guy thing 😛
It抯 actually a great and helpful piece of info. I am glad that you shared this useful info with us. Please keep us up to date like this. Thanks for sharing.
Sure thing! Thanks
Thanks for this amazing article. I am loving it. keep the awesome work.
Hi! I’m at work browsing your blog from my new iphone! Just wanted to say I love reading through your blog and look forward to all your posts! Carry on the superb work!