
Google Hacking: Google Dorks
Before jumping straight to Google Hacking and what are Dorks let me just give you and overview of the world we live in right now. Today, we live in an era of Information Warfare. The places you visit, the food you eat, your daily habits, pretty much everything is available on the Internet for anyone and everyone to see. All those naive Social Media posts and selfies which you thought are cool, can be used to basically draft all your behavioural patterns and could possibly be used against you without you not having the slightest clue about that! Sounds scary right? It indeed is.

Image Courtesy: Google
Here, you’ll learn about one such stupidly simple method by which you can gather specific targeted information about any Person or rather an Organization. Google Hacking (or Dorking) will not only help in improving your Ethical Hacking skills but also in your everyday Google Searches. So Google Hacking, what is it? Let’s see!
What is Google Hacking or Google Dorks?
 Image Courtesy: Google
Image Courtesy: Google
This was basically introduced in 2002 by a man named Johnny Lang when he started leveraging custom queries to find Sensitive Information about his Target. According to Wiki, Google Hacking, also named Google Dorking, is a computer hacking technique that uses Google Search and other Google applications to find security holes in the configuration and computer code that websites use.
Simply put, we can use Google Hacking to find Sensitive Information being leaked, Usernames and Passwords, Vulnerabilities in Web Applications, Unauthorized access on certain web pages and a whole lot more. This happens because as google indexes all the web pages, certain pages are often not (or less) accessed by consumers over the internet. This makes them rank very low in Google results and thus stays extremely far from the topmost found result.
Using Google Hacking or Dorks, we can specifically target to find a particular type of data and thus eliminate all the unnecessary results which aren’t important to us.
The best part about Google Hacking is that it is extremely passive and completely legal as we are only accessing publicly available information. Nonetheless, if you do any malicious stuff with that information, that’d definitely be termed illegal!
How to actually perform Google Hacking?

Image Courtesy: Google
So there are basically different types of Operators which are used for this purpose of Google Hacking. Each Operator is used in association with the particular query to be searched for. The basic syntax for a particular dork goes as follows:
Operator_Name:<Search Query>Operators used for Google Hacking

Image Courtesy: Google
There are a number of available Operators. Let’s take a look at them!
- site: Limits the search to a specific site.
Eg.site:twitter.com shows only results from twitter.com and nothing else
- intitle: Shows only the sites containing the query in their title text.
- allintitle: Same as intitle but will look for the exact match as the specified terms
Eg. intitle:Login Page will only show pages having Login Page in their Title text
- inurl: Looks for specified term in the URL.
- allinurl: Same as inurl but searches for the exact match as the specified terms
Eg. inurl:?id=1 will display only the URLs having ?id= in them
- filetype or ext: Searches only for the specified filetype/extension.
Eg. ext:ppt will display only powerpoint presentations in the results
- intext: Searches the query terms in the content of the page.
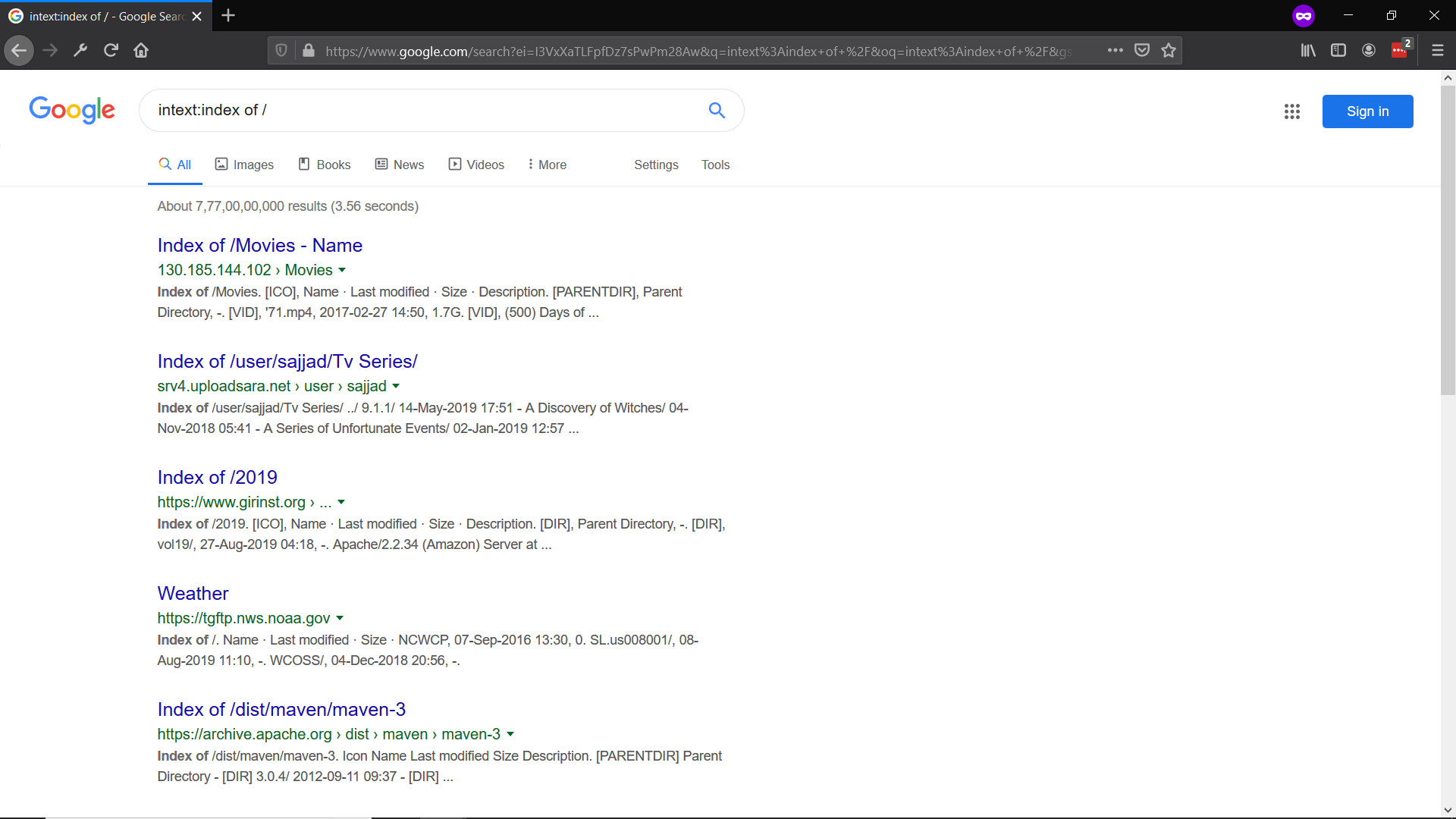
Eg. intext:Index of / will throw all the sites having that keyword in their html
These are the most basic ones which you’ll probably need. Nonetheless, there are many more of these including maps, books, link, etc. which you can further look into!
Advanced Dork Usage and Examples

Image Courtesy: Google
Now that you know all about Dorks and the involved operators, let’s take a step further and mix match those operators. Above all, ready for some fun? Let’s go!
You can basically use any number of operators in conjunction to get more precise and accurate results.
site:.pk inurl:?id=1
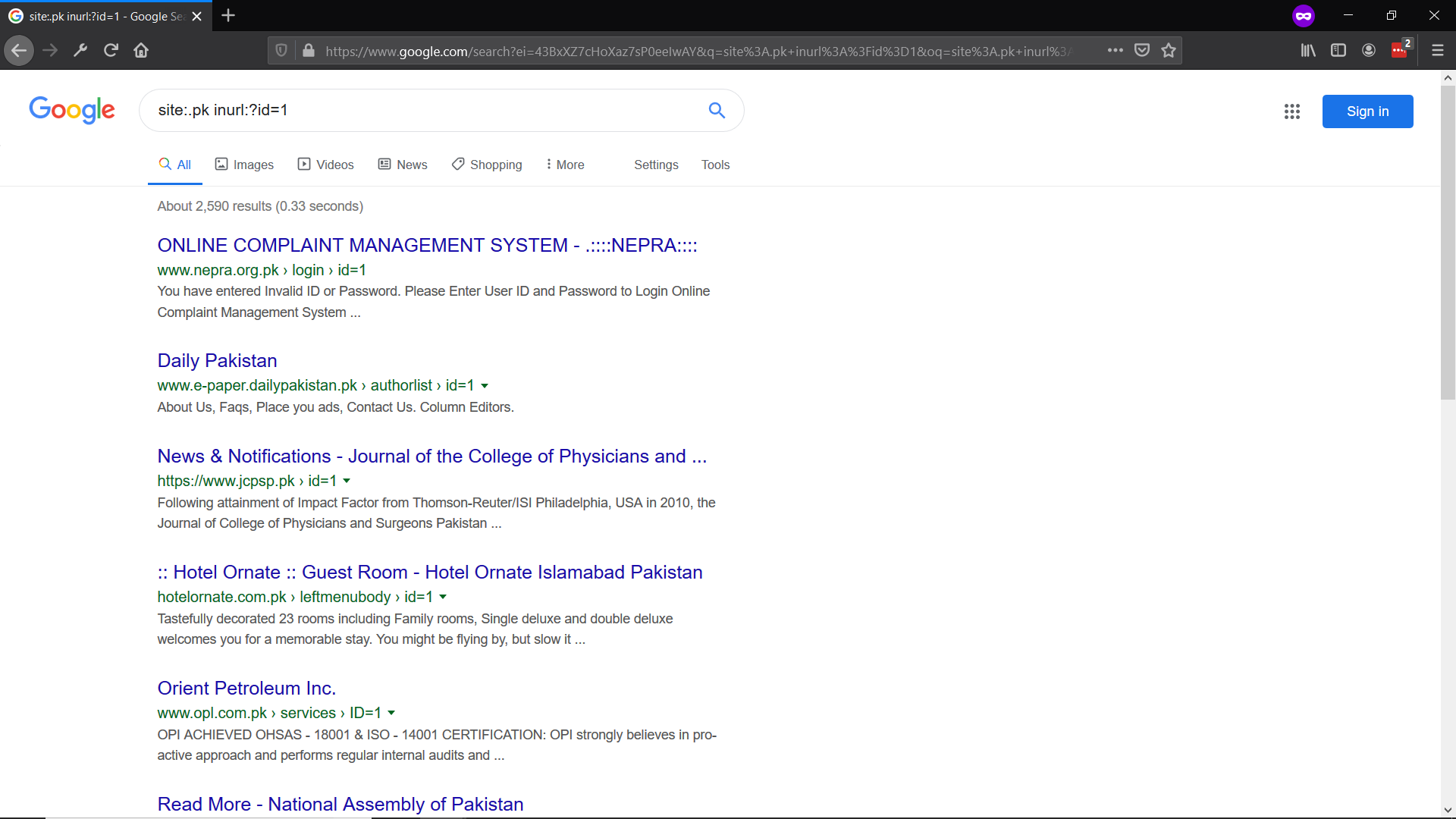
intext:hacking ext:pdf
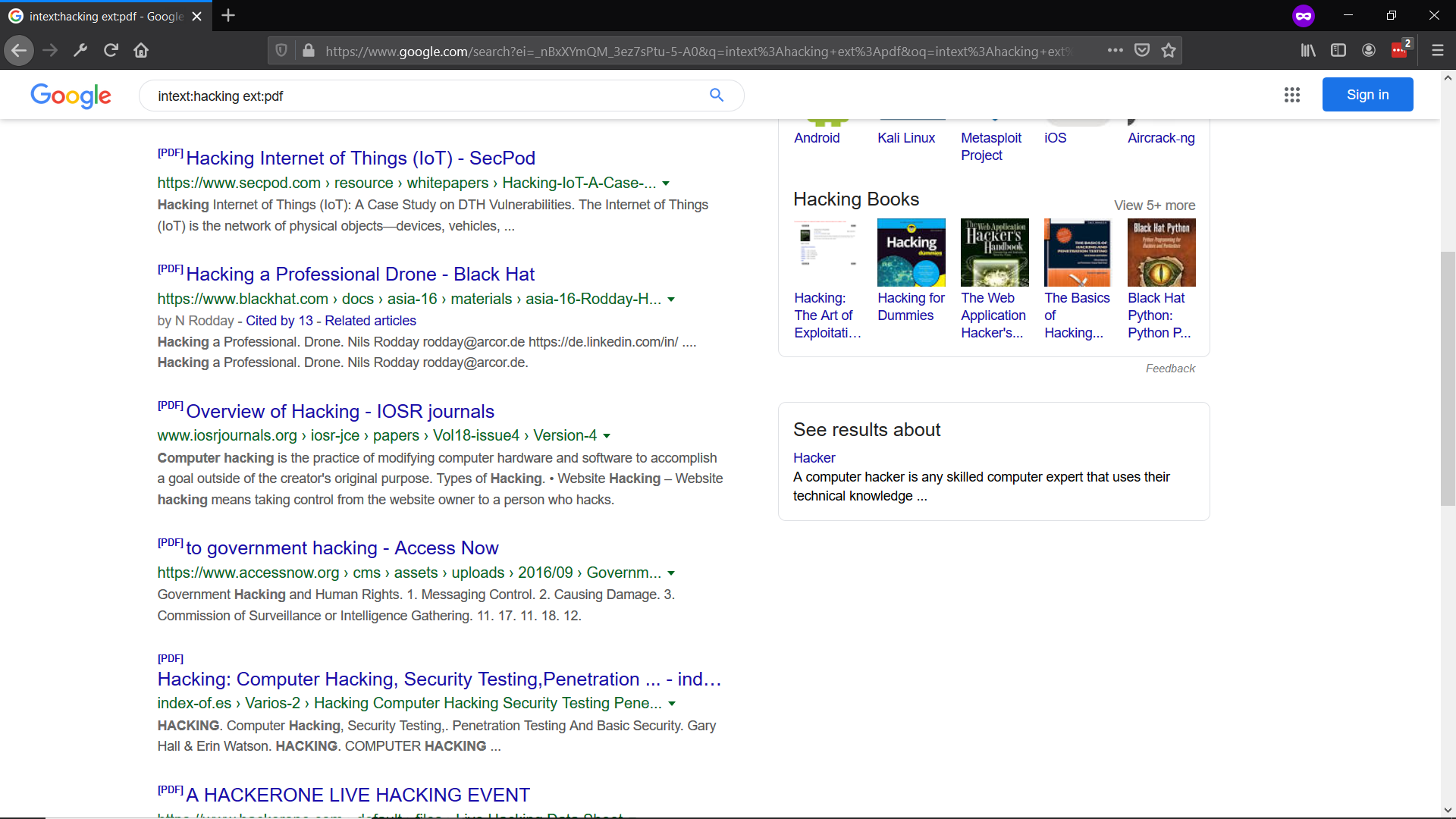
intext:index of /
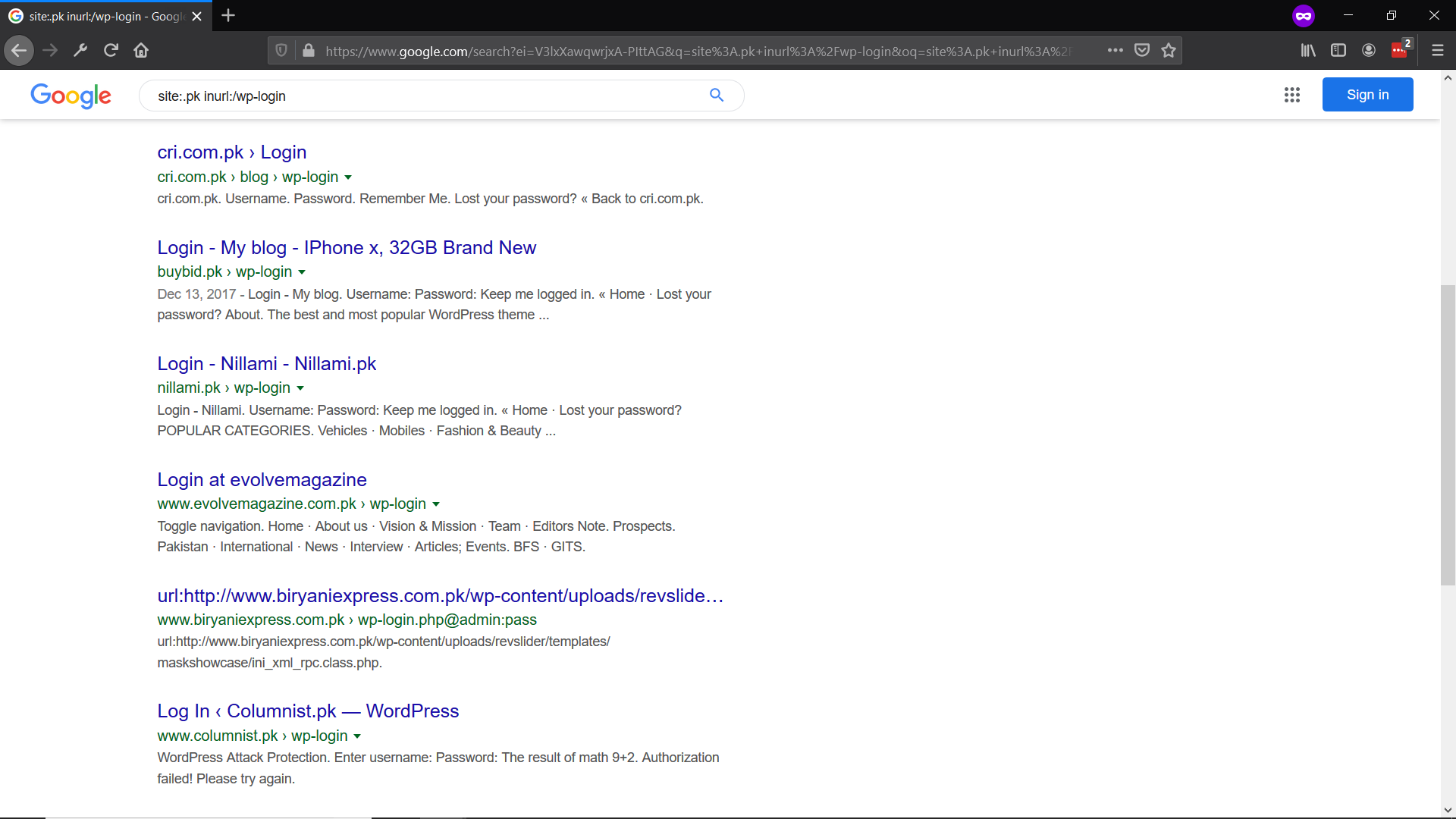
inurl:/wp-admin
Summary and Conclusion

Image Courtesy: Google
Thus, these were some pretty basic yet extremely powerful ways in which you can use Google Hacking. This makes it a great tool for your Recon and in fact might directly lead to Vulnerabilities without any exploitation at all!
If you wish to further deep dive into Google Hacking and Dorking, here are some links that might help.
Furthermore, the rest is onto your imagination! So, this was all about Google Hacking. Now shoot off, try out this newly learned arsenal added to your Hacker Skillset in the wild and share your results in the comments section. The HackrSpace signing off for now, but a lot more is yet to come. Meanwhile Keep Hacking! and Stay tuned 🙂

Great content! Super high-quality! Keep it up! 🙂
Thank you for your kind words 🙂